《计算机应用》唯一官方网站 ›› 2024, Vol. 44 ›› Issue (4): 1107-1113.DOI: 10.11772/j.issn.1001-9081.2023050563
所属专题: 人工智能
收稿日期:2023-05-10
修回日期:2023-07-17
接受日期:2023-07-24
发布日期:2023-08-01
出版日期:2024-04-10
通讯作者:
孟华
作者简介:王杰(1997—),女,四川广元人,硕士研究生,主要研究方向:拓扑数据分析、机器学习基金资助:Received:2023-05-10
Revised:2023-07-17
Accepted:2023-07-24
Online:2023-08-01
Published:2024-04-10
Contact:
Hua MENG
About author:WANG Jie, born in 1997, M. S. candidate. Her research interests include topological data analysis,machine learning.Supported by:摘要:
卷积神经网络(CNN)参数众多、分类边界复杂,对数据的局部特征较敏感,导致当CNN模型受到对抗攻击时,精度明显下降;而拓扑数据分析(TDA)方法更关注数据的宏观特征,天然具有对抗噪声和梯度攻击的能力。为此,提出一种耦合拓扑数据分析和CNN的图像分类算法MCN(Mapper-Combined neural Network)。首先,利用Mapper算法得到刻画数据集宏观特征的Mapper图,通过多视图的Mapper图对每一个样本点进行新的特征表示,并将新特征表示成二值向量;其次,结合新特征和CNN提取的隐藏层特征,增强隐藏层特征;最后,使用特征增强后的样本数据训练全连接的分类网络,完成图像分类任务。在MNIST和FashionMNIST数据集上,将MCN与纯卷积网络、单一Mapper特征分类算法进行对比,采用主成分分析(PCA)降维的MCN的初始分类精度提升了4.65%和8.05%;采用线性判别分析(LDA)降维的MCN的初始分类精度提高了8.21%和5.70%。实验结果表明,MCN分类精度更高,并且对抗攻击能力更强。
中图分类号:
王杰, 孟华. 基于点云整体拓扑结构的图像分类算法[J]. 计算机应用, 2024, 44(4): 1107-1113.
Jie WANG, Hua MENG. Image classification algorithm based on overall topological structure of point cloud[J]. Journal of Computer Applications, 2024, 44(4): 1107-1113.

图1 Fashion-MNIST数据受扰动前后第9类(短靴)的局部卷积特征分布和全局拓扑特征分布
Fig. 1 Local convolutional feature distribution and global topological feature distribution of ninth type (ankle boot) in Fashion-MNIST data before and after disturbance
| 方法 | MNIST | Fashion-MNIST |
|---|---|---|
| CNN | 97.80 | 85.56 |
| MCN(PCA) | 98.39 | 88.32 |
| Mapper-P | 94.02 | 81.74 |
| MCN(LDA) | 97.82 | 85.99 |
| Mapper-L | 90.40 | 81.36 |
表1 初始分类精度 (%)
Tab. 1 Initial classification accuracy
| 方法 | MNIST | Fashion-MNIST |
|---|---|---|
| CNN | 97.80 | 85.56 |
| MCN(PCA) | 98.39 | 88.32 |
| Mapper-P | 94.02 | 81.74 |
| MCN(LDA) | 97.82 | 85.99 |
| Mapper-L | 90.40 | 81.36 |

图6 Fashion-MNIST数据在4种噪声扰动下的归一化精度(投影方式采用PCA)
Fig. 6 Normalization accuracy of Fashion-MNIST data under four noise disturbances with projection method of PCA
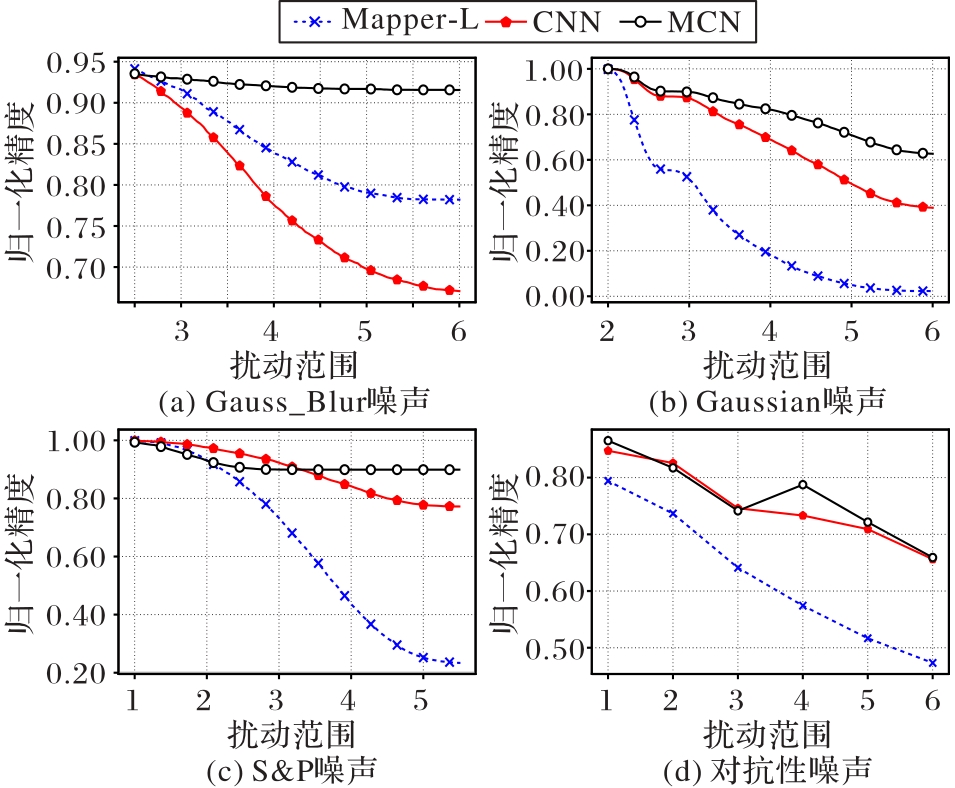
图8 Fashion-MNIST数据在4种噪声扰动下的归一化精度(投影方式采用LDA)
Fig. 8 Normalization accuracy of Fashion-MNIST data under four noise disturbances with projection method of LDA
| 1 | MIKA S, SCHÖLKOPF B, SMOLA A, et al. Kernel PCA and de-noising in feature spaces [C]// Proceedings of the 11th International Conference on Neural Information Processing Systems. Cambridge: MIT Press, 1998:536-542. |
| 2 | YANG J, FRANGI A F, YANG J-Y, et al. KPCA plus LDA: a complete kernel Fisher discriminant framework for feature extraction and recognition [J]. IEEE Transactions on Pattern Analysis and Machine Intelligence, 2005, 27(2): 230-244. 10.1109/tpami.2005.33 |
| 3 | RIFAI S, VINCENT P, MULLER X, et al. Contractive auto-encoders: explicit invariance during feature extraction[C]// Proceedings of the 28th International Conference on Machine Learning. Madison: Omnipress, 2011: 833-840. 10.1007/978-3-642-23783-6_41 |
| 4 | PHAM D, LE T. Auto-encoding variational Bayes for inferring topics and visualization[C]// Proceedings of the 28th International Conference on Computational Linguistics. London: International Committee on Computational Linguistics, 2020: 5223-5234. 10.18653/v1/2020.coling-main.458 |
| 5 | LeCUN Y, BOTTOU L, BENGIO Y, et al. Gradient-based learning applied to document recognition[J]. Proceedings of the IEEE, 1998, 86(11):2278-2324. 10.1109/5.726791 |
| 6 | LIU Y, YAO X. Optimisation and learning in neural network learning[C]// Proceedings of the 2003 IASTED International Conference on Modelling, Simulation and Optimization. Calgary, Canada: IASTED, 2003:167-172. |
| 7 | SZEGEDY C, ZAREMBA W, SUTSKEVER I, et al. Intriguing properties of neural networks[EB/OL]. [2023-05-01]. . |
| 8 | XU K, ZHANG G, LIU S, et al. Adversarial T-shirt! evading person detectors in a physical world[C]// Proceedings of the 16th European Conference on Computer Vision. Berlin: Springer, 2020: 665-681. 10.1007/978-3-030-58558-7_39 |
| 9 | JING P, TANG Q, DU Y, et al. Too good to be safe: tricking lane detection in autonomous driving with crafted perturbations[C]// Proceedings of 30th USENIX Security Symposium. Berkeley: USENIX Association, 2021: 3237-3254. |
| 10 | XIE C, WU Y, VAN DER MAATEN L, et al. Feature denoising for improving adversarial robustness[C]// Proceedings of the 2019 IEEE/CVF Conference on Computer Vision and Pattern Recognition. Piscataway: IEEE, 2019:501-509. 10.1109/cvpr.2019.00059 |
| 11 | RONY J, HAFEMANN L G, OLIVEIRA L S, et al. Decoupling direction and norm for efficient gradient-based L2 adversarial attacks and defenses[C]// Proceedings of the 2019 IEEE/CVF Conference on Computer Vision and Pattern Recognition. Piscataway: IEEE, 2019:4322-4330. 10.1109/cvpr.2019.00445 |
| 12 | CARLSSON G. Topological pattern recognition for point cloud data[J]. Acta Numerica, 2014, 23: 289-368. 10.1017/s0962492914000051 |
| 13 | NIELSON J L, PAQUETTE J, LIU A W, et al. Topological data analysis for discovery in preclinical spinal cord injury and traumatic brain injury[J]. Nature Communications, 2015, 6: 8581. 10.1038/ncomms9581 |
| 14 | SINGH G, MÉMOLI F, CARLSSON G E. Topological methods for the analysis of high dimensional data sets and 3D object recognition[C]// Proceedings of the 2007 Eurographics Symposium on Point-Based Graphics. Eindhoven, The Netherlands: Eurographics Association, 2007: 91-100. |
| 15 | LONGCOPE D W. Topological methods for the analysis of solar magnetic fields[J]. Living Reviews in Solar Physics, 2005, 2: 7. 10.12942/lrsp-2005-7 |
| 16 | ALMGREN K, KIM M, LEE J. Extracting knowledge from the geometric shape of social network data using topological data analysis[J]. Entropy, 2017, 19(7): 360. 10.3390/e19070360 |
| 17 | ROSSI-deVRIES J, PEDOIA V, SAMAAN M A, et al. Using multidimensional topological data analysis to identify traits of hip osteoarthritis[J]. Journal of Magnetic Resonance Imaging, 2018, 48(4): 1046-1058. 10.1002/jmri.26029 |
| 18 | CYRANKA J, GEORGES A, MEYER D. Mapper based classifier[C]// Proceedings of the 2019 18th IEEE International Conference on Machine Learning and Applications. Piscataway: IEEE, 2019: 1099-1106. 10.1109/icmla.2019.00184 |
| 19 | COHEN G, AFSHAR S, TAPSON J, et al. EMNIST: extending MNIST to handwritten letters[C]// Proceedings of the 2017 International Joint Conference on Neural Networks. Piscataway: IEEE, 2017: 2921-2926. 10.1109/ijcnn.2017.7966217 |
| 20 | TANG Y, CUI H, LIU S. Optimal design of deep residual network based on image classification of Fashion-MNIST dataset[J]. Journal of Physics Conference Series, 2020, 1624:052011. 10.1088/1742-6596/1624/5/052011 |
| 21 | PAPERNOT N, MCDANIEL P, WU X, et al. Distillation as a defense to adversarial perturbations against deep neural networks[C]// Proceedings of the 2016 IEEE Symposium on Security and Privacy. Washington, DC: IEEE Computer Society, 2016: 582-597. 10.1109/sp.2016.41 |
| 22 | TRAMÈR F, KURAKIN A, PAPERNOT N, et al. Ensemble adversarial training: attacks and defenses[C/OL]// Proceedings of the 2018 International Conference on Learning Representations. Rosten, VA:The Internet Society [2023-05-01]. . |
| 23 | GU S, RIGAZIO L. Towards deep neural network architectures robust to adversarial examples[C/OL]// Proceedings of the 2015 International Conference on Learning Representations [2023-05-01]. . |
| 24 | XU W, EVANS D, QI Y. Feature squeezing: detecting adversarial examples in deep neural networks[C/OL]// Proceedings of the 2018 Network and Distributed System Security Symposium. Rosten, VA:The Internet Society [2023-05-01]. . 10.14722/ndss.2018.23198 |
| 25 | BHATTACHARYA S, GHRIST R, KUMAR V. Persistent homology for path planning in uncertain environments[J]. IEEE Transactions on Robotics, 2017, 31(3): 578-590. 10.1109/TRO.2015.2412051 |
| 26 | DE SILVA V, GHRIST R. Coverage in sensor networks via persistent homology[J]. Algebraic & Geometric Topology, 2007, 7(1): 339-358. 10.2140/agt.2007.7.339 |
| 27 | EDELSBRUNNER H, LETSCHER D, ZOMORODIAN A. Topological persistence and simplification[J]. Discrete & Computational Geometry, 2002, 28(4):511-533. 10.1007/s00454-002-2885-2 |
| 28 | MILNOR J W, SPIVAK M, WELLS R, et al. Morse Theory[M]. Princeton: Princeton University Press, 1963:1-133. |
| 29 | NICOLAU M, LEVINE A J, CARLSSON G. Topology based data analysis identifies a subgroup of breast cancers with a unique mutational profile and excellent survival[J]. Proceedings of the National Academy of Sciences, 2011, 108(17): 7265-7270. 10.1073/pnas.1102826108 |
| 30 | LUM P Y, SINGH G, LEHMAN A, et al. Extracting insights from the shape of complex data using topology[J]. Scientific Reports, 2013, 3: 1236. 10.1038/srep01236 |
| 31 | 张德学. 一般拓扑学基础[M]. 北京:科学出版社, 2012:62-70. |
| ZHANG D X. Fundamentals of General Topology[M]. Beijing: Science Press, 2012:62-70. | |
| 32 | HATCHER A. Algebraic Topology[M]. Cambridge: Cambridge University Press, 2002:754-756. |
| 33 | ZOMORODIAN A, CARLSSON G. Computing persistent homology[C]// Proceedings of the 20th Annual Symposium on Computational Geometry. New York: ACM, 2004: 347-356. 10.1145/997817.997870 |
| 34 | DONG Y, LIAO F, PANG T, et al. Boosting adversarial attacks with momentum[C]// Proceedings of the 2018 IEEE/CVF Conference on Computer Vision and Pattern Recognition. Washington, DC: IEEE Computer Society, 2018: 9185-9193. 10.1109/cvpr.2018.00957 |
| [1] | 秦璟, 秦志光, 李发礼, 彭悦恒. 基于概率稀疏自注意力神经网络的重性抑郁疾患诊断[J]. 《计算机应用》唯一官方网站, 2024, 44(9): 2970-2974. |
| [2] | 李云, 王富铕, 井佩光, 王粟, 肖澳. 基于不确定度感知的帧关联短视频事件检测方法[J]. 《计算机应用》唯一官方网站, 2024, 44(9): 2903-2910. |
| [3] | 李顺勇, 李师毅, 胥瑞, 赵兴旺. 基于自注意力融合的不完整多视图聚类算法[J]. 《计算机应用》唯一官方网站, 2024, 44(9): 2696-2703. |
| [4] | 赵宇博, 张丽萍, 闫盛, 侯敏, 高茂. 基于改进分段卷积神经网络和知识蒸馏的学科知识实体间关系抽取[J]. 《计算机应用》唯一官方网站, 2024, 44(8): 2421-2429. |
| [5] | 陈虹, 齐兵, 金海波, 武聪, 张立昂. 融合1D-CNN与BiGRU的类不平衡流量异常检测[J]. 《计算机应用》唯一官方网站, 2024, 44(8): 2493-2499. |
| [6] | 张春雪, 仇丽青, 孙承爱, 荆彩霞. 基于两阶段动态兴趣识别的购买行为预测模型[J]. 《计算机应用》唯一官方网站, 2024, 44(8): 2365-2371. |
| [7] | 王东炜, 刘柏辰, 韩志, 王艳美, 唐延东. 基于低秩分解和向量量化的深度网络压缩方法[J]. 《计算机应用》唯一官方网站, 2024, 44(7): 1987-1994. |
| [8] | 高阳峄, 雷涛, 杜晓刚, 李岁永, 王营博, 闵重丹. 基于像素距离图和四维动态卷积网络的密集人群计数与定位方法[J]. 《计算机应用》唯一官方网站, 2024, 44(7): 2233-2242. |
| [9] | 董瑶, 付怡雪, 董永峰, 史进, 陈晨. 不完整多视图聚类综述[J]. 《计算机应用》唯一官方网站, 2024, 44(6): 1673-1682. |
| [10] | 黄梦源, 常侃, 凌铭阳, 韦新杰, 覃团发. 基于层间引导的低光照图像渐进增强算法[J]. 《计算机应用》唯一官方网站, 2024, 44(6): 1911-1919. |
| [11] | 李健京, 李贯峰, 秦飞舟, 李卫军. 基于不确定知识图谱嵌入的多关系近似推理模型[J]. 《计算机应用》唯一官方网站, 2024, 44(6): 1751-1759. |
| [12] | 沈君凤, 周星辰, 汤灿. 基于改进的提示学习方法的双通道情感分析模型[J]. 《计算机应用》唯一官方网站, 2024, 44(6): 1796-1806. |
| [13] | 姚迅, 秦忠正, 杨捷. 生成式标签对抗的文本分类模型[J]. 《计算机应用》唯一官方网站, 2024, 44(6): 1781-1785. |
| [14] | 高文烁, 陈晓云. 基于节点结构的点云分类网络[J]. 《计算机应用》唯一官方网站, 2024, 44(5): 1471-1478. |
| [15] | 孙敏, 成倩, 丁希宁. 基于CBAM-CGRU-SVM的Android恶意软件检测方法[J]. 《计算机应用》唯一官方网站, 2024, 44(5): 1539-1545. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||
